One Piece World
Sunday, February 6, 2011
Domain Hacking
Domain Hijack ing is a process by which Internet Domain Names are stolen from it’s legitimate owners. Domain Hijack ing is also known as Domain theft. Before we can proceed to know How to Hijack Domain names, it is necessary to understand How the Domain names operate and How they get associated with a particular web server (website).
The operation of Domain name is as follows
Any website say for example gohacking.com consists of two parts. The Domain name (gohacking.com) and the web hosting server where the files of the website are actually hosted. In reality, the Domain name and the web hosting server (web server) are two different parts and hence they must be integrated before a website can operate successfully. The integration of Domain name with the web hosting server is done as follows.
1. After registering a new Domain name, we get a control panel where in we can have a full control of the Domain .
2. From this Domain control panel, we point our Domain name to the web server where the website’s files are actually hosted.
For a clear understanding let me take up a small example.
John registers a new Domain “abc.com” from an X Domain registration company. He also purchases a hosting plan from Y hosting company. He uploads all of his files (.html, .php, javascripts etc.) to his web server (at Y). From the Domain control panel (of X) he configures his Domain name “abc.com” to point to his web server (of Y). Now whenever an Internet user types “abc.com”, the Domain name “abc.com” is resolved to the target web server and the web page is displayed. This is How a website actually works.
What happens when a Domain is Hijack ed
Now let’s see what happens when a Domain name is Hijack ed. To Hijack a Domain name you just need to get access to the Domain control panel and point the Domain name to some other web server other than the original one. So to Hijack a Domain you need not gain access to the target web server.
For example, a hacker gets access to the Domain control panel of “abc.com”. From here the hacker re-configures the Domain name to point it to some other web server (Z). Now whenever an Internet user tries to access “abc.com” he is taken to the hacker’s website (Z) and not to John’s original site (Y).
In this case the John’s Domain name (abc.com) is said to be Hijack ed.
How the Domain names are Hijack ed
To Hijack a Domain name, it’s necessary to gain access to the Domain control panel of the target Domain . For this you need the following ingredients
1. The Domain registrar name for the target Domain .
2. The administrative email address associated with the target Domain .
These information can be obtained by accessing the WHOIS data of the target Domain . To get access the WHOIS data, goto whois.Domain tools.com, enter the target Domain name and click on Lookup. Once the whois data is loaded, scroll down and you’ll see Whois Record. Under this you’ll get the “Administrative contact email address”.
To get the Domain registrar name, look for something like this under the Whois Record. “Registration Service Provided By: XYZ Company”. Here XYZ Company is the Domain registrar. In case if you don’t find this, then scroll up and you’ll see ICANN Registrar under the “Registry Data”. In this case, the ICANN registrar is the actual Domain registrar.
The administrative email address associated with the Domain is the backdoor to Hijack the Domain name. It is the key to unlock the Domain control panel. So to take full control of the Domain , the hacker will hack the administrative email associated with it. Email hacking has been discussed in my previous post How to hack an email account.
Once the hacker take full control of this email account, he will visit the Domain registrar’s website and click on forgot password in the login page. There he will be asked to enter either the Domain name or the administrative email address to initiate the password reset process. Once this is done all the details to reset the password will be sent to the administrative email address. Since the hacker has the access to this email account he can easily reset the password of Domain control panel. After resetting the password, he logs into the control panel with the new password and from there he can Hijack the Domain within minutes.
How to protect the Domain name from being Hijack ed
The best way to protect the Domain name is to protect the administrative email account associated with the Domain . If you loose this email account, you loose your Domain . So refer my previous post on How to protect your email account from being hacked. Another best way to protect your Domain is to go for private Domain registration. When you register a Domain name using the private registration option, all your personal details such as your name, address, phone and administrative email address are hidden from the public. So when a hacker performs a WHOIS lookup for you Domain name, he will not be able to find your name, phone and administrative email address. So the private registration provides an extra security and protects your privacy. Private Domain registration costs a bit extra amount but is really worth for it’s advantages. Every Domain registrar provides an option to go for private registration, so when you purchase a new Domain make sure that you select the private registration option.
How to set up a phising website !
on Sep 12 in IT, The Internet tagged disclaimer, howto, long, phishing, rogue by Chris
I realize that we’re probably going to get flagged for this big-time, but just to clear things up: this may not necessarily be strictly for malicious purposes, nor is it intended to be (the full disclaimer is at the end of this article). This is a simple guide for setting up a phishing website using strictly free software, intended as both educational and even useful in some circumstances.
The Required Software
We will be using this software for this guide:
- The Apache Websever
- Optional: DNS Server Software, e.g. BIND or PowerDNS
Apache Configuration
The crux of this tutorial centers around configuring Apache to “be” a certain website. For this example, we want to masquerade as Google. The first step is to configure Apache to pretend to be the site we wish to masquerade as, from the machine destined to be the phishing server.
The Apache master host configuration file (which is the traditional/deprecated httpd.conf within your installation directory) should have sections such as this for each website you wish to masquerade as:
(note that the paths are relative to a Unix/Linux installation; modify them for your system; comments are everything after the ‘#’ character for clarification)
NameVirtualHost: *:80 # Any hostname/IP, TCP port 80 (default for HTTP) # Virtual Host delimiter, e.g. a website under this installation ServerName www.google.com # main website name ServerAlias google.com google.com. www.google.com. *.google.com # Any other name for Google.com DocumentRoot /var/www/google # where the fake website's pages are stored # Per-directory configuration directives Options FollowSymLinks MultiViews AllowOverride None Order allow,deny allow from all # we phish for anyone, you could modify this for only select hosts, however CustomLog /var/log/apache2/google.log combined # log the visits to the fake website With Apache’s httpd.conf containing that, and optionally some other Apache optimization within the other configuration files, a service restart will make the fake site (Google in this case) “live”, but without any content or visitors.
Appearing as the intended site
In our configuration file, we told Apache that any requests for “Google.com” from our server should be directed to the “/var/www/google” directory for content (which should be empty). In order to appear as Google to the visitors we wish to phish, we need Google’s content within this directory.
The easiest way to retrieve content from the existing website is via the “wget” command, which is standard on Linux/Unix installations (Windows users can simply visit the page and save it directly to the content folder instead). For our example, our wget command:
user@Phisher:/var/www/google$ wget -O index.html http://www.google.com/
…would retrieve Google’s home page and store it within the file index.html within the content directory used by Apache2 for requests made to “Google.com” to our server. Keep in mind that “index.html” is (by default) the file sent to the users’ browser when a request is made to the root directory ‘/’ of a site.
Tailoring
Before we get to the step of directing users to our Google.com instead of Google’s Google.com, we should modify the site’s content so we can retrieve (phish) the content we want.
This is where this could easily turn malicious, and I would like to remind you, dear non-malicious reader, of the extensive disclaimer at the end of this article.
As a non-malicious example, we will pretend we are a parent seeking to monitor Google searches from a network of children (a very probable and applicable scenario). All that is required is a little modification of the index.html file, and/or creation of a Google-compliant search.php file.
Although the access logs for the server would suffice (providing IP information to identify the searcher), you will still probably want to return real Google results so as to convince the visitors that this is the real Google website.
Modifying the “form” HTML element to point to an alternative search processing file may be necessary, while in most cases it would suffice to create your own “search.php” file (with the Apache PHP module installed) to process search queries and retrieve results from Google.
Easiest way to retrieve search queries from Google is probably to pass the query string from your phishing site’s search.php as HTTP POST data to http://www.scroogle.org/cgi-bin/nbbw.cgi, and using some simple XML parsing and formatting to present the results in a results page that exactly mimics Google’s.
That last bit requires a bit of PHP/Perl programming skill (over the head of most parents I know), and represents the biggest challenge in phishing: changing the pages to get what you want.
Redirecting Visitors To Your Site
At this stage, your Apache server installation should be set up and ready to serve up requests aimed for the site you’re masquerading as, and it the content for the site should be filled with content that looks exactly like the real site, only providing you with the data the user thinks they are entering on the real site.
Now, for the process of sending users to your site instead of the real one: simple DNS manipulation.
DNS Re-cap: The Internet’s DNS (Domain Name System) is the process of translating a domain name (e.g. Google.com) into a routable IP Address, e.g. 70.89.148.9 or 192.168.3.1. As Apache’s virtual host system permits, multiple domain names can resolve to the same IP Address for the serving of separate web (HTTP) content.
In short, you need to make your target machines manually resolve “Google.com” (as in our example) to the IP address of your phishing server.
This means that you can’t make the entire Internet redirect a given domain name to your site, at least not without severe and easily-detectable DNS hijacking. Instead, you should focus on your target set of hosts, i.e. the children in our parenting example we explained earlier.
To do this manually, you must modify the host file of each system. The host file is a manually-editable “database” of domain names and their corresponding IP addresses, and takes authority over DNS queries to a remote system.
On Windows systems, this file is located at “C:\Windows\System32\drivers\etc\hosts”, and on Linux/Unix/Macintosh systems this file is at “/etc/hosts”. The format is extremely basic, with examples in both as to how to statically enter DNS entries.
On Windows systems, after entering this information, it is necessary to execute the command “ipconfig -flushdns” to clear the memory-cached DNS resolution entries so the new changes can take effect.
While this method works, it is not practical for, says, 5-100 hosts. In that case, it is then necessary to simply add a real DNS server to the network using one of the free tools mentioned above. I won’t go into detail as to configuring an individual piece of DNS server software to resolve a domain to your phishing server’s IP (RTFM), but I will tell how to make the server’s resolutions take effect for the whole network.
Most networks, especially those within homes, have a DHCP server, many times integrated into their router. Simply place the IP Address of your new rogue DNS server (presumably the same as your web server) to the top of the list of DNS servers within your DHCP parameters, and following the next renewal, your server will take the top authority for DNS resolutions for your network (other than the host file).
There is also a way to, using a *nix router, manually route all traffic to a host for processing – see theUpside-down-ternet page for these details (and for a guide to dick around with wardrivers).
What you’ve done…
…is this: everytime someone requests (in this example) Google.com, either a rogue DNS server you set up or a host’s host file will resolve the domain name to the IP address of your phishing server, which will accept the request and serve up content from a directory containing content that appears as the targeted site, only with some other purpose for your benefit.
There may be other ways to set this up, but this is certainly the fastest. Keep in mind that if your server goes down, all queries will still go to the real site unless you de-listed all DNS servers except the rogue one you set up.
Other Suggestions
Instead of drastically modifying the content for your site, for example if you wish to simply have a static web history via access logs, then you could simply make your rogue DNS server (via wildcards) resolve alltraffic to your phishing server, which simply retrieves the target content via wget and serves it to the client.
To accomplish this proxy solution, you would need to modify the VirtualHost directive to make the 404 (not found) error page the same page as the “index.php” page, which calls and processes the wget script (I recommend using stdout to redirect the content from wget to the browser as opposed to saving every piece of content to a file before serving it)
Also, please note that none of this guide applies to secure (HTTPS) websites. HTTPS communication takes place on port 443 instead of port 80, and there is a solid authentication process for verifying secure sites as opposed to insecure sites.
* Disclaimer *
Don’t use this guide for malicious purposes, despite how easily this guide could be adopted for such goals. The example I used throughout the article was for a parent wishing to monitor children’s Google searches, and as such any possible malicious purposes are not in any way implied.
We have no affiliation with Google, inc. We simply used their site as an example to phish because they are very popular and a parent may wish to monitor a child’s Google activity, realistically.
If you get detained for phishing, or any other criminal activity for that matter, then the mere visit to this page does not place any of the blame on us: you chose to do whatever you did based on your own decision.
This guide is educational only, and should not be interpreted as an invitation to violate one’s privacy.
Don’t be a jerk.
Friday, December 4, 2009
Sunday, December 7, 2008
Nibiru



Nibiru, to the Babylonians, was the celestial body associated with the god Marduk. The name is Akkadian and means 'crossing place' or 'place of transition'. In most Babylonian texts it is identified with the planet Jupiter. In Tablet 5 of the Enuma Elish it may be the pole star, which at the time was Thuban or possibly Kochab (Ursa Minor).
The term "Nibiru" comes from the Sumerian cuneiform tablets and writings dating 5,000 years old. The term Nibiru means "Planet of the crossing", and it's cuneiform sign was often a cross, or various winged disc. The Sumerian culture was located in the fertile lands between the Euphrates and Tigris rivers, at the southern part of today's Iraq.
Due to its use in opposition to the phrase itebbiru "who used to cross," Landsberger and Kinnier Wilson suggest that it refers to a stationary point in the heavens.1 In a reconstruction of Tablet V of the Enûma Elish by Landsberger and Kinnier Wilson, the word ni-bi-ri (variant: ni-bi-ru and ni-bi-a-na) is translated as "pole star."1 The authors add in the footnotes that "Applied to Marduk, there is no question that in the late periods neberu is a planet, whether Jupiter or Mercury" however for the referenced translation of Tablet V, "pole star" is used.
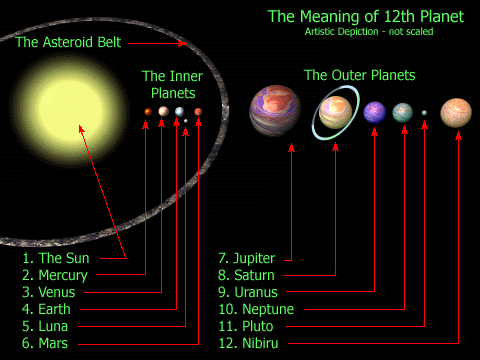
Some authors believe that the observations of ancient astronomers provide proof that Nibiru is an actual planet or brown dwarf in our solar system. These claims are for the most part dismissed as fringe science or pseudoscience by the mainstream scientific communities of archaeology and astronomy.

According to proponents such as renowned historian, Hebrew scholar, author, speaker and archaeologist Zecharia Sitchin and Burak Eldem the Nibiru appearing in Sumerian records correctly refers to a large planetary body. Their research proposes that it possesses a highly elliptical, 3630-year orbit. Such a planet would be approximately in the same orbit as 2000 CR105.
According to these theories of Sumerian cosmology, Nibiru was the twelfth member in the solar system family of planets (which includes 10 planets, the Sun, and the Moon). Its catastrophic collision with Tiamat, a planet that was between Mars and Jupiter, would have formed the planet Earth, the asteroid belt, and the Moon.
This was the result of one of Nibiru's host satellites colliding with Tiamat, appropriately leaving half a planet, comparable to our Pangea (our current knowledge of all the continents as one land mass), and leaving deeps rifts in the crust beneath the Pacific ocean. It was until recently thought impossible for such large celestial bodies to collide due to intense magnetic force, however, this concept has been given a new life since the introduction of the Orpheus Theory, and the simulation of a collision between objects such as our own earth, and an object half it's size.
It was the home of a technologically advanced human-like alien race, the Anunnaki of Sumerian myth, who, Sitchin claims, survived and later came to Earth. Sitchin has also transcribed that their travelling to earth was the result of their failing atmosphere (having since been drawn into our solar system from its cosmic passing, the atmosphere of Nibiru was subjected to intense external stress from our sun).
They came in search of gold particles used for their reflective properties (recognized even today by Nasa who plate various objects including astronaut helmet eyeshields) to place in their atmosphere. According to Sitchin, they subsequently genetically engineered our species, originally as slave workers to work in their gold mines, by crossing their genes with those of Homo erectus.
The Anunnaki ("those who from heaven came to earth" in Sumerian) came upon evolution on earth as it had been progressing for billions of years however, they desired to create a worker who could communicate and learn from them. After a slew of failed prototypes an Anunnaki goddess engineered a perfect specimen- the Adam. This was done using 80% of the Inferior specimen and 20% of the superior Anunnaki specimen. It is only recently that we understand DNA as having a double-helix nature, The Sumerians depicted their goddess creator along with snakes in a double helix form with thin bars connecting between them in a spiral fashion. The intertwined snakes are also modern day representatives for the field of medicine.
Sitchin says some sources speak about the same planet, possibly being a brown dwarf star and still in a highly elliptic orbit around the Sun, with a perihelion passage some 3,600 years ago and assumed orbital period of about 3,600 to 3,760 years or 3,741 years.
Sitchin attributes these figures to astronomers of the Maya civilization. Many involved in research of this kind predict a return date of Nibiru passing Earth coinciding with the Winter Solstice of 2012; specifically at 11.11 UT, 21st December 12, 2012.
This also coincides with a rare alignment of the Earth, Sun and centre of the Milky Way , and is asserted to be likely to cause a pole shift. However, scientists argue that a planet with such an orbit would eventually either develop a circular orbit or fly off into space and overwhelmingly consider Sitchin's claims to be pseudoscience.
The similar orbit of 2000 CR105, however, is accepted by scientists. A brown dwarf with a period of 3,760 years would be clearly evident through infrared and gravitational observations. And it has been. In 1993 Nasa launched the IRAS telescope which picked up the faint image of a large celestial body 3 times the distance of Pluto in our own solar system. In the press conference, the two scientists one named Gerry Neugebauer said that these objects could be "almost anything, from a tenth planet in our solar system to distant galaxies".
Later much deeper images were taken, and some of the objects were found to be dense gas clouds in our own Galaxy, while others turned out to be very distant galaxies. In fact, these observations heralded the discovery of a new type of object: Ultra-luminous Infrared Galaxies (ULIRGs).
These are galaxies in which there is a burst of stars being born. The cocoons of dust in which the stars are enshrouded generates copious infrared, which is what was detected by IRAS. They published these results in the prestigious Astrophysical Journal.
Another interesting discovery also brought Nibiru into light recently. Eris, the largest known dwarf planet has been discovered on the 21st of October 2003, announced in July 2005 and officially named from 2003 UB313 to "136199 Eris" in 2006.
Originally it was considered as the tenth planet of our Solar System, but in April 2006, according to the new, more precise definition of the term "planet", it has been designated as a "dwarf planet" along with Pluto and Ceres. Eris has an orbital period of 556.7 years, and currently lies at almost its maximum possible distance from the Sun (aphelion) and will enter Pisces in 2036.
Eris: More Massive than Pluto NASA - June 19, 2007
Pluto Smaller Than Nearby Dwarf Planet Eris, Study Finds National Geographic - June 15, 2007
Pluto is now 134340 - Xena is now Eris National Geographic - September 16, 2006
Wednesday, October 1, 2008
what's happened last summer .. ?
well ,, last summer it's the best summer ever 4 me ..everyday playing Truth or Dare .. and do crazy things ..
mmm ,, a lot of crazy things ,,the Japanese concert ,lunch at Italian pizza ,going 2 the baleh and Via Via night ... mm what else ohh ,, i act doctor 4 something like an hour & go to workshop for 3 days and live in 4 star hotel with great food & awesome chef .. etc ,,
well,, i just wanna thanx my friends for the awesome things that we done together ..
thanx 2 u all my friends :D
Mute :My secrets box :D
Zeze :The one with big head ^^'
Sadaqa : Bnfhm 3a ba3ad kteer ..
Bebe : the lovely one in Luffy's 9..
Malak : the good one ..
Moni : our big brother & the strong one ...
Fefe : Mashtoob Luffy's 9 ..
Nana : the most cute personalty i ever know ..
Sesa : my favorite gurl ^^;
& u 2 guys i hope that we 'll be great friends 4 ever ..
Shado : great guy ..
Hadeel : hey u i missed u a lot ..
Lyal : my Ex babe :P
Wala2 : i hope that we 'll be great friends..
Dana: the most funny gurl i ever know ^^;
Dido : the new gurl...
M.d :it's really nice 2 meet yea :D
3adi : lol i love this gurl ..
Raheel :great personalty & kteer bt5af ^^'
Lubna : cute lovely & we hea z3laneh btd7k ..
Ahmed(naruto) : byzkrni b7ali wana z3'eer ..
Finaly i just wanna say sorry 2 u all ,,, if i do anything wrong with anyone..
please forgive me ...
Wednesday, June 11, 2008
My new Lists,, Anime & Drama
1.one piece
2.Bleach
3.Narouto
4.Naruto Shippoden
5.The law of Ueki
6.Moshishi[x 1]
7.school rumble season 1
8.school rumble season 2
9.Black Lagoon
10.Eyeshield 21 [1-53]
11.Fate stay night[x 2]
12.Midori No Hibi
13.Genshiken[o]
14.GTO
15.karas
16.The skull Man[x 3]
17.ef a tale of memories
18.afro samurai
19.noir[x 4]
20.Black cat
21.Gun x Sword[x 5]
22.Yami[x]
23.Onigai Twins[o]
24.seto no hanayome[x 6]
25.Death Note
26.DN Angel
27.Wolfs Rain
28.oran hight school host club
29.fruits basket
30.X samurai
31.Hunter x Hunter [1-62]
32.Hunter x Hunter ova1+2+3
33.Elfen lide
34. Now and then here and there
35.Full Metal Alchimest
36.Devil May Cry[x 7]
37.Code Geass
38.Darcker Than BLack[o]
39.Ghost Hunt
40.Romeo x Julit
41.melanholy of haruni suzumiya[o]
42.air
43.AAnH[x 8]
44.Full metal panic
45.Gun selenger girl[x 9]
45.tide line blue[x 10]
46.jyu oh ji[x 11]
47.GunGrave
48.Blasilsk[o]
49.Heroic Age
50.T BLooD[x 12]
51.Lovly Complex
52.Tsubasa_Chronicle season 1[x 13]
53.Tsubasa_Chronicle season 2[x]
54.Tsubasa_Chronicle OVA'z[x]
55.Mushi-Uta[x 14]
56.Hikaru no go [o]
57.Slam Dunk
58.Dear boys
59.Kanon
///Drama Lis
1.Hana Yori Dango season 1
2.Hana Yori Dango season 2
3.Gokusen season 1
4.Gokusen season 2
5.1 Litre Of Tears
6.Dragon Zakura
7.My Boss My Hero
8.Hanazakari.no.Kimitachi
9.Liar Game
10.Kurosagi
11.Nobuta wo Produce
12.Proposal Daisakusen
13.unfair
14.Tatta Hitotsu no Koi
15.yamada tarou
16.hanayomi wo yaludeshi
17.Dear Student
Thursday, May 22, 2008
Besara7a m3 el wakeel

اذاعة القوات المسلحة الاردنية من راديو فن اف ام..من الساعه السابعة والربع الى العاشره الا ربع ...برنامج بصراحة مع الوكيل..يقدمة المقدم الفذ محمد الوكيل....يبحث هذا البرنامج بمشاكل المواطنيين الاردنيين مع الحكومه ......<<<ما بعرف اشرح

سكان الاردن بيسمعو هاد البرنامج وانا منهم<<<مع العلم انو في كتير من خارج الاردن...بتعرفو ليش بسمع هالبرنامج ؟؟! عشان اعرف اعيش هداك اليوم...لما تسمعه هاد البرنامج بيعطيك دفعه معنوية مش طبيعيه <<هاد بيرجع ل طبيعة مقد البرنامج و الاغاني الوطنية الي بتضلها ع مدار الساعتين....

من الاخر:على ما اعتقد انو كتير كويس للاردنين الي عايشين برا الاردن ....!!

انت بتسمعوو وازا بتسمعوو احكيلي كيف ؟؟
وازا ما سمعتو حاول اسمعوو و اعطينا رأيك ..!!
وبس
